Active directory is arguably the most important part of your IT infrastructure – housing all user accounts and password data in a centralized place. Due to its very nature, ensuring the Active Directory is secure is both a complex and necessary task. To protect yourself against insider threats it is important to make sure you keep track of all activities and changes that occur in the past and present in your Active Directory through in-depth reporting and real-time alerting.
How to track, audit and monitor Active Directory activities and modifications
There are two main techniques for auditing Active Directory – native auditing and third party solutions.1. Native Auditing
Auditing the Active Directory natively involves enabling the “audit object changes” option in Active Directory Domain Services. This feature can be implemented by enabling the Global Audit Policy and configuring the System Access Control List. By doing this, you can generate audit logs which can be tracked in the event viewer. To avoid generating an excessive number of logs, create audit exceptions through schema.In previous versions of Windows Server, audit logs provided information solely on who made changes to which active directory object attributes. From Windows Server 2008 onwards, enabling auditing creates logs of old and new values as well.
Although these audit logs do display a substantial amount of information, using native processes like “Event Viewer” or “PowerShell” can be both a time consuming and ineffective method. This is mainly due to the lack of reports, alerts and graphical comparisons that you can get from the tools. For example, in order to perform historical change tracking, you have to manually compile audit data for each change and list them to make comparisons. This is essentially a full time job if you intend to perform regular and in-depth audits.
2. Third Party Solutions
Third party solutions can help you address all manner of security, systems management and compliance challenges by pro-actively auditing, monitoring and alerting on critical IT systems. LepideAuditor for Active Directory automates the auditing of Active Directory and provides over 270 pre-defined reports that can be delivered via the console or to any specified email address. Deploying an automated solution like this ensures that you get the maximum detail from your audits with the minimum amount of effort.Below are some examples of the customized reports generated by LepideAuditor for Active Directory that can be used to track, monitor and alert on historic events/activities happening within the Active Directory:
Report I – The following image depicts three trends (in graphical view) as a result of the past events/activities in the Active Directory, including:
1. User Modifications Trend – This displays important operations performed by users, such as create, delete, modify, rename, move, security changes and permissions modifications.
2. Computer Modifications Trend – This report displays computer operations, such as create, delete, modify, move, rename, status change and permission modifications.
3. Group Modifications Trend – This graph shows all the operations performed on specific or numerous groups (a group of user accounts) such as create, delete, modify, rename, move, permission change and membership information (including the addition of new users and deletion of some users).
By hovering over the values you can obtain further details on the information displayed in the graph.

In addition to this, LepideAuditor for Active Directory can also generate detailed reports that show any changes in the usual trends of permissions being granted to users. This includes permission analysis of the historic events/activities in the Active Directory.
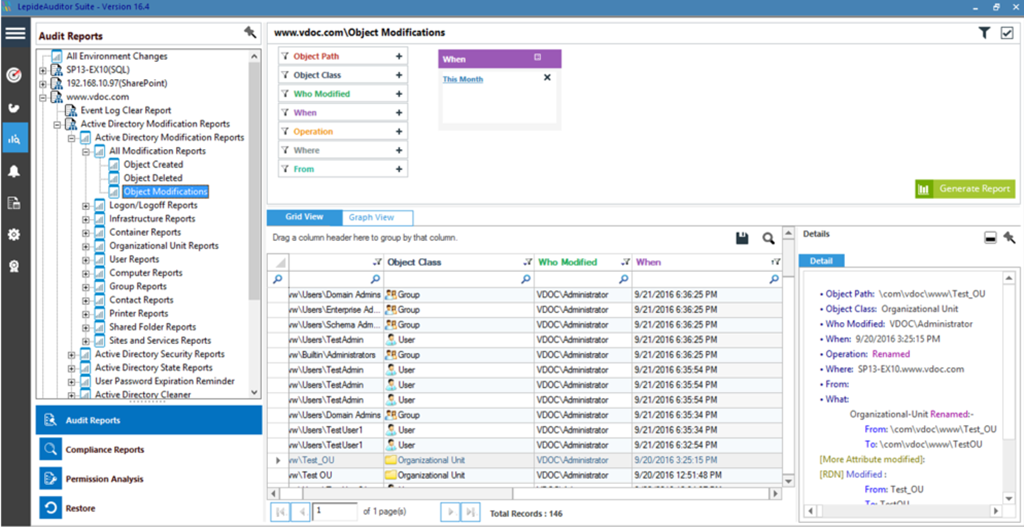
Report II – The below report shows domain modifications made by users in an easy to view grid alongside details regarding users whose accounts have been created. You can delve deeper into the reports by filtering based on user path, who created the account, when the account is created, where it is created, “from” field and more. In this image, the custom filters “this month” and “administrator” have been applied to generate a report of the administrator’s activities in the current month.
The detail of each row in the report is displayed on the right hand side under the “Detail” column, as shown in the image.

LepideAuditor Suite includes numerous exclusive features designed specifically to ensure that users are provided with complete visibility into activities taking place in the Active Directory. Some of these include the following:
1. All Modification Reports for Active Directory
LepideAuditor Suite tracks Active Directory modifications and displays all potential changes, along with before and after values, for the objects being modified.2. Real-time Alerting
Whenever any suspicious behavior, activity or event is encountered in the Active Directory environment, LepideAuditor Suite sends real-time alerts in three different ways: Email notifications (sent straight to the inbox), LiveFeed alerts that continuously track changes as they happen and the LepideAuditor app – a mobile application that allows users to receive instant alerts straight to any Apple or Android enabled device.
3. Powerful Search Capability
LepideAuditor Suite possesses a powerful search functionality that allows users to locate relevant data quickly and easily. All searches can be saved directly to the console for future reference.Conclusion
Securing your Active Directory is a critical part of your IT security plan, and tracking the changes (both current and historical) that your users are making in this system is a reliable method of detecting suspicious activity. Third-party solutions, like LepideAuditor for Active Directory, provide you with a 360-degree view (both graphical and grid based) of all the events happening within your Active Directory – including displaying “who,” “what,” “when” and “where” details for all changes made. By automating the auditing of your critical IT systems you can ensure that you are getting the maximum amount of detail with the minimum amount of effort.This article was written by Satyendra Tiwari for The Funky Tech Guy. Follow him on twitter @satylepide

 Popular
Popular
 Tags
Tags
 Videos
Videos









0 comments :
Post a Comment